A Complete Guide to DevSecOps: What, Why, and How
DevOps adoption, if done correctly, should yield positive effects for any company, including improved team cooperation, shorter time to market, increased overall productivity, and increased customer happiness, to mention a few.
But what good will all of these advantages do for your organization if security isn’t a top priority? Trying to push water uphill with a rake while focusing on DevOps to enhance your workflow is like trying to push water uphill with a rake.
The “Sec” in DevSecOps, on the other hand, can act as the Robin to your DevOps Batman, giving constant backup. This post will lead you through the entire process of developing your own DevSecOps framework.
The Traditional Approach to Security
Organizations used to do security tests on their products at the end of the software development life cycle before DevOps (SDLC). Because the emphasis was primarily on application development, security was considered less vital than the previous stages. By the time engineers did security tests, the goods had progressed through the majority of the previous stages and were nearly complete. As a result, detecting a security problem at such a late stage necessitated altering innumerable lines of code, an excruciatingly time-consuming and arduous operation. Patching became the chosen solution, which is unsurprising. As a result, security was considered as only a gut feeling that nothing would go wrong, rather than investing the time and money required to concretely strengthen it in the pipeline.
Where and How It All Went Wrong
In the previous ten years, IT infrastructure has advanced dramatically. The majority of security and compliance monitoring technologies, on the other hand, have not progressed in the same way. As a result, most technologies are unable to test code as quickly as a typical DevOps environment requires.
In addition, cybercrime is on the rise at an alarming rate. According to Juniper Research, the average cost of a single data breach will be more than $150 million by 2020 as more company infrastructures become connected to one another.
DevSecOps has a direct positive impact because it aids in the management of these potentially disastrous situations.
What Is DevSecOps?
Every step of the DevOps process should be secure.
To most firms, “rapid and secure code delivery” may be an oxymoron. DevSecOps, on the other hand, wants to shift that perception.
DevSecOps is a way of thinking about IT security in which “everyone is responsible for security.” It entails incorporating security procedures into a company’s DevOps workflow. The goal is to incorporate security into the software development process at every stage. That’s in contrast to previous development models—DevSecOps implies that security isn’t saved till the end of the SDLC.
If your firm already uses DevOps, you should think about switching to DevSecOps. DevSecOps is founded on the DevOps idea at its core, which can assist you make the case for switching. And by doing so, you’ll be able to bring together skilled professionals from many technical disciplines to improve your current security processes.
Myths about DevSecOps
Anti-patterns are frequent in buzzwords, and DevSecOps is no exception. Let’s take a look at some frequent misunderstandings.
Myth 1: For DevSecOps, we Need “Super Developers”!
Not at all. You’re erroneous if you believe that DevSecOps requires special folks with magical coding skills. You don’t need to put on your hiring hat just yet unless you can’t properly train your existing staff or your developers aren’t interested in making the DevSecOps change. The goal of DevSecOps is to break down silos. Your development team, which will be made up of employees with a variety of skill sets, will be trained in DevSecOps processes and techniques that will last throughout your delivery pipeline. As a result, you’ll be combining current teams rather than hiring a new one.
Myth 2: DevSecOps Can Take the Place of Agile
It’s not possible. DevSecOps is a supplement to agile, not a replacement. In order for enterprises to optimize their business benefits, they must coexist. Agile encourages teamwork and continuous feedback. It does not, however, cover software delivery through testing, QA, and production, unlike DevSecOps. DevSecOps rounds out the picture by giving methodologies and tools to help with agile changes.
Myth 3: DevSecOps can be purchased
No, not at all. You can only acquire tools for the process, such as release management and continuous integration and delivery (CI/CD) tools. Because DevSecOps is a philosophy and not a methodology, you can’t buy the full process. The things that actually make a difference in your business—team collaboration and an emphasis on team accountability and ownership—aren’t things you can buy.
What Qualities Should a DevSecOps Engineer Have?
DevSecOps engineers are growing increasingly in demand as more businesses recognise their importance. What will the finest ones have to offer?
A few more skill sets are required for the role of a DevSecOps engineer. A solid understanding of DevOps ideas, techniques, and culture is required. Languages such as Python, Java, and Ruby should be well-understood by candidates. Chef, Puppet, Checkmarx, and ThreatModeler are just a few of the programs that a skilled DevSecOps engineer will be familiar with.
Aside from that, DevSecOps experts must understand the nuances of risk assessment and threat modelling. They’ll have up-to-date understanding of cybersecurity dangers, best practices, and other related software. And, in terms of work experience, DevSecOps is, of course, fantastic. Prior expertise in non-DevOps IT security, on the other hand, can be a good predictor of future DevSecOps success.
DevSecOps Best Practices
The following aspects help and play a vital part in DevSecOps implementation.
Practice Secure Coding
The capacity to design software that is highly resistant to vulnerabilities is an evident benefit of safe coding. Without secure code, a variety of software security threats, such as a breach of a company’s confidential information, can arise. As a result, it’s critical that your engineers are capable of doing so—even if it means investing time and money. Setting and adhering to coding standards is also beneficial because it aids developers in writing clean code.
Embrace Automation
Automation is an important characteristic of DevSecOps, just as it is in DevOps. In order to keep up with the velocity of code delivery in a CI/CD system, security automation is required. This is especially true in large businesses, where engineers frequently push different versions of code to production.
When automating security testing, it’s crucial to think about what you’re doing. Using the incorrect automated tools for the wrong tasks might be disastrous. To continuously examine and identify any potential risks early in the development cycle, static application security testing (SAST) tools are generally utilized. It’s critical to pick the proper security automation tool and stick with it if you want your company’s products to succeed.
Shift Left
Instead of waiting till the end of the delivery chain, the shift left testing strategy involves incorporating security into your apps from the start. The apparent benefit is that you will be able to discover possible vulnerabilities sooner and work on correcting them. And the sooner you uncover any issues, the less expensive it will be to correct them. As a result, it’s a fantastic practice, but it’s not without its drawbacks. Shifting left may momentarily disturb your present DevOps process workflow, which is a regular issue. It may be difficult to overcome this, but if you implement DevSecOps, shifting left is undoubtedly a better practice in the long term.
People, Process, and Technology
People
It doesn’t matter how excellent you are at the other things; if your people aren’t interested, you won’t be able to build a mature, effective DevSecOps environment. It may be difficult to persuade top management to make the change. However, the fact that high-profile data breaches are common as a result of ineffective protection could support your argument. In order to get your DevSecOps correctly, you’ll need security experts and “security champions.”
Process
Many components make up a process. Workflow standardization and documentation are the most crucial. Typically, distinct procedures are carried out by separate teams inside a company. However, DevSecOps argues for defining and executing processes that are widely agreed upon in order to increase the level of security in development.
Technology
People are more equipped to perform DevSecOps processes with the help of technology. Automation and configuration management, Security as Code, automated compliance scans, host hardening, and other technologies are commonly utilized in DevSecOps methods.
How to Implement DevSecOps
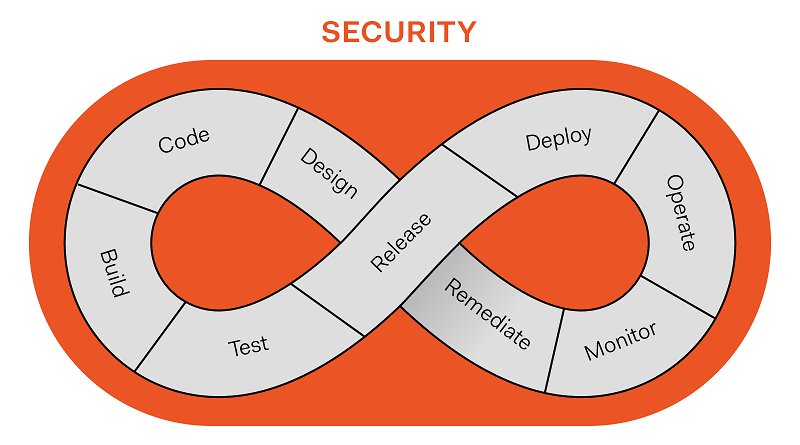
Implementing DevSecOps is a lengthy process, as you might anticipate. I’ll now walk you through the eight steps of adopting DevSecOps. The following processes are frequently present, even if there aren’t any clear, sequential phases that serve as a road map.
Planning and Development
It all begins with preparation. The plan must be smart and succinct in order to be implemented successfully. Simple feature descriptions will not suffice. Acceptance test criteria, user designs, and threat models must all be established by the pros.
The next stage is development, and teams should begin by assessing the maturity of their current processes. To provide guidance, it’s a good idea to gather information from a variety of sources. Establishing a code review mechanism at this time may also be beneficial because it promotes uniformity, which is a DevSecOps feature.
Building and Testing
Then there’s building, which is handled by automated build tools. The source code is combined into machine code in such tools via a build script. Build automation software includes a number of useful capabilities. They have a large library of plugins and a variety of UIs to choose from. Some can also automatically discover and replace any insecure libraries with new ones.
The next phase is testing, where the pipeline is instilled with solid testing principles thanks to the comprehensive automated testing framework.
Deployment and Operation
IaC tools are commonly used for deployment since they automate the process and speed up software delivery.
Another critical step is operation, and operations staff are responsible for routine maintenance. Zero-day exploits are a nightmare. As a result, operating teams should keep an eye on them. DevSecOps can use IaC tools to secure the organization’s infrastructure fast and efficiently, preventing human mistake.
Monitoring and Scaling
Using strong, continuous monitoring tools is also a vital component of the process. They make sure your security systems are working properly.
Scaling has an essential part as well. Because to the development of virtualization, businesses no longer have to waste resources on maintaining massive data centers. Instead, they may simply extend the IT infrastructure to manage any dangers that arise.
These are some of the fundamental processes in implementing DevSecOps. Your road plan may include certain particular additional steps, depending on the size and complexity of the project.
DevSecOps Challenges
Of course, implementation comes with a string of challenges.
Cultural Challenges
The most significant roadblock that most organizations have in adopting a DevSecOps strategy is the resistance they may encounter. Many people will be hesitant to make a significant adjustment to something they’ve been doing for years. And the fact that security was an afterthought in previous software development approaches doesn’t help matters.
DevSecOps also brings together developers and security experts, fostering a collaborative atmosphere. However, there has always been some tension between these two sides. Both teams believe that what the other team does causes problems for their own. This viewpoint leads to both teams functioning in silos, which contradicts DevSecOps’ main principle. To mature in implementation, a shift in this cultural perspective is required once again.
Another major stumbling block is the perception that higher security slows things down and prevents innovation. Developers strive to provide code quickly in order to fulfil the demands of modern organizations. Security teams, on the other hand, are primarily concerned with ensuring that the code is secure. Because their goals are so dissimilar, it’s difficult for these two teams to work together.
Other Challenges
By 2021, there will be 3.5 million cybersecurity employment openings, according to a forecast by Cybersecurity Ventures. As a result, despite the fact that the number of security breaches and attacks is increasing, there is a scarcity of experienced cybersecurity engineers. As a result, the scarcity of security personnel is a problem that particularly impacts small and medium-sized businesses.
When it comes to bringing together ops and security, there are more challenges than when it comes to cooperation between development and security. You just need to train your developers about security best practices and have them collaborate closely with your security team in the first case. Although this structure affects developers in various ways, there are usually few noticeable changes.
When it comes to getting your operations and security teams to work together, however, this isn’t the case. When ops engineers notice something unusual, they don’t instantly suspect a security compromise. Things like software misconfiguration or infrastructure issues are often culprits for them. An anomaly, on the other hand, signals a potential breach to security teams. As a result, ops engineers may need to reconsider how they examine environments.
DevSecOps Benefits
DevSecOps can help you sell more of your products. The most obvious and fundamental advantage of a DevSecOps approach is that it will increase your overall security. As previously said, you may uncover vulnerabilities in your pipeline at a very early stage, making it much easier to resolve. It also improves your threat-hunting capabilities because constant monitoring is in place. In terms of business, the safer a product is, the easier it is to market.
When vulnerabilities are discovered early in the SDLC process, the costs of repairing them are greatly reduced. Bringing together multiple teams to work on security promotes accountability. This type of collaboration also makes it easier to develop quick and effective security response tactics as well as more secure security design patterns.
DevSecOps also reduces the occurrence of security bottlenecks. It’s not necessary to wait until the development cycle is complete before performing security checks. These two elements hasten the delivery of a product.
Another area in which DevSecOps is crucial is ensuring compliance with industry-standard rules. Regulations such as the General Data Protection Regulation (GDPR) require considerable caution while managing data. DevSecOps gives managers with a comprehensive overview of such procedures, allowing for easier compliance.
It’s Time to Revolutionize Your Security
There’s no denying that DevSecOps is changing the way businesses approach security. Many mid- and low-level businesses, however, are still apprehensive of moving to DevSecOps for a variety of reasons, including a lack of awareness of what DevSecOps is, an unwelcome culture shift for employees, funding constraints, and sometimes just the ambiguity of the phrase.
The technical and financial benefits that organizations can gain from using DevSecOps are quite promising. Although there will undoubtedly be some setbacks when you first begin, DevSecOps can be extremely beneficial to your firm in the long term.









Leave a Reply