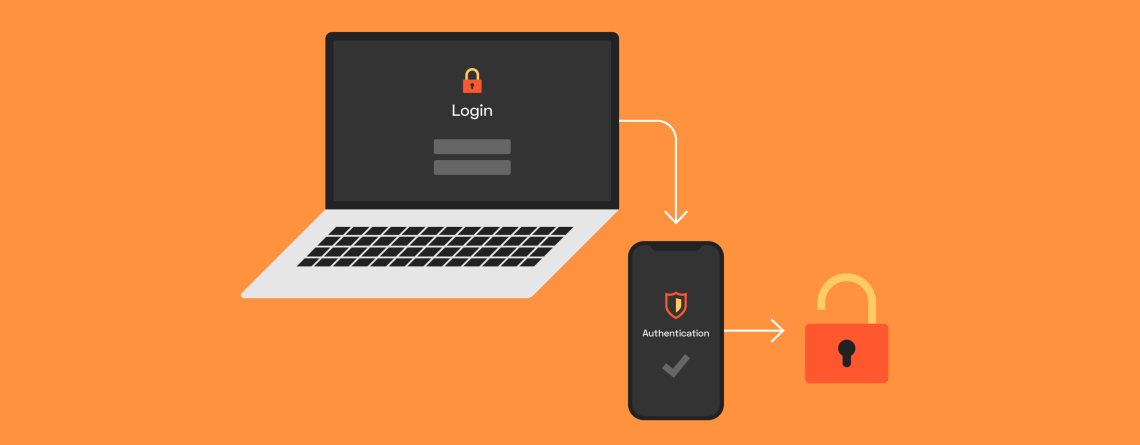
What’s Multifactor Authentication?
Passwords, as you may know, are one of the most commonly used security mechanisms for securing a device. To secure our systems, we employ a variety of passwords. However, in today’s network world, passwords are vulnerable to attack. Additional security measures are required. This is accomplished through the use of multifactor authentication. So, what exactly is Multifactor Authentication (MFA)? This mechanism is essentially a security system that identifies the user using more than one authentication method. This mechanism acts as a second or additional barrier against the attackers.
Multifactor Authentication employs a variety of mechanisms. Multifactor Authentication, on the other hand, combines two or more of these mechanisms. These mechanisms are as follows:
- Information known by the user like passwords
- Information owned by the user like security tokens
- Information specific to user body like fingerprints
- Information about user location
- Information about user access time
Various platforms are involved in this network security job with Multifactor authentication methods. Mobile phones or emails, for example, can be used for this authentication. When the user attempts to log into the device, a text message or an email can be sent to him. The access code can be included in emails and messages using this second step. This mechanism is widely used in many fields today.
Aside from using additional devices, our bodies can also be used to identify and authenticate us. As you are aware, the human body contains identical parts such as the voice, fingerprints, retinas, and so on. Users can authenticate themselves by verifying such biometric information.
Why We Need Multifactor Authentication?
Multifactor Authentication adds another layer of defense against any attacker. In today’s world, traditional password security mechanisms are insufficient to secure our networks. There are several flaws in this password protection.
User information is stored in authentication databases, as you are aware. In other words, authentication servers have username and password lists. Storing all of this information is risky because if someone gets their hands on these credentials, they can easily use these user credentials to gain access to the systems. This is one of the weaknesses of traditional password protection.
Another flaw in password protection concerns password strings. Previously, we used weak passwords to gain access to network devices. Then we began to use strong passwords. These strong passwords may be sufficient to prevent brute force attacks. However, CPU capacities are rapidly increasing, providing more capacity for brute force attacks. As a result, attackers can attempt millions of passwords per second.
Multifactor Authentication assists us in overcoming these flaws. We can improve the security of our network devices by implementing additional security barriers in addition to password protection.
Multifactor Authentication Factor
The category of credentials that can be checked during authentication is known as Multifactor Authentication Factor. What exactly are the Multifactor Authentication Factors?
These elements are as follows:
- Knowledge Factors
- Possession Factors
- Inherence Factors
- Location Factors
- Time Factors
Knowledge Factors are factors that are related to user knowledge. This can include a user password, security questions, a security shape, and so on.
Possession Factors are those that have to do with additional platforms. This can be a smartphone, email, SMS, or other device. One of these platforms receives a second code.
Inherence Factors are factors that are related to the body. This can include fingerprints, retina, iris, voice, and so on. The user can authenticate using these identical parts.
Location Factors are factors that are related to your location. GPS is used to determine location. This enables authentication in specific areas.
Time Factors are factors relating to access time. This enables authentication only at specific times.











Leave a Reply